Logon via Remote Desktop
This section describes the procedure for logging on to a remote PC via a remote desktop connection.
Prerequisites
- The software must be installed on the destination PC.
- The authenticator registration must have been completed.
- The “Limited sign-in options” policy must be enabled.
- Both source and destination OS must be Windows 10, Windows 11, or WindowsServer 2022 or later.
If the authenticator is not yet registered
You may be forced to register your authenticator when logging on (administrator setting).
In such cases, follow the on-screen instructions to register the authenticator.
Start the Remote Desktop application and connect to the PC you wish to log on to.
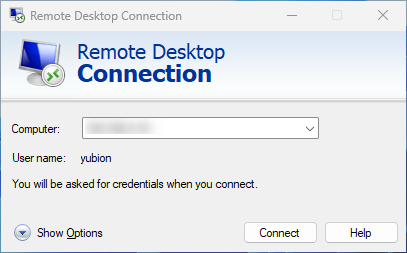
If Network Level Authentication (NLA) for Remote Desktop Connection is enabled, please connect to Remote Desktop by specifying the user name and password of the PC you wish to log on.
YubiOn FIDO Logon is a product that customizes the authentication on the logon screen after connecting to Remote Desktop, so the conventional Windows standard authentication is used for the authentication when connecting to Remote Desktop.
If network level authentication is enabled, the logon user after remote desktop connection is fixed to the user specified in network level authentication.
Other than this specified user, the FIDO Logon logon will not appear.
If network level authentication is disabled, the user name is basically specified on the logon screen after connecting. (Click here for details)
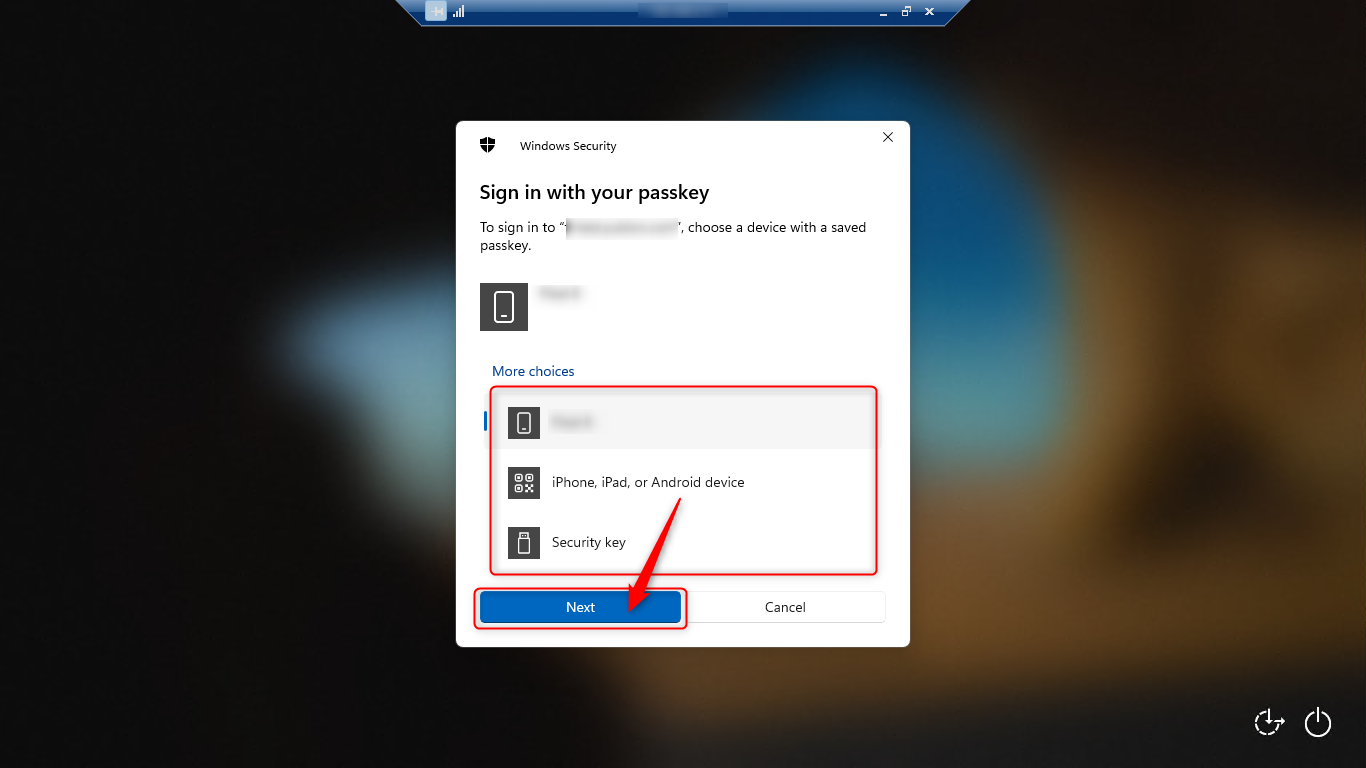
When the source PC is Windows 11
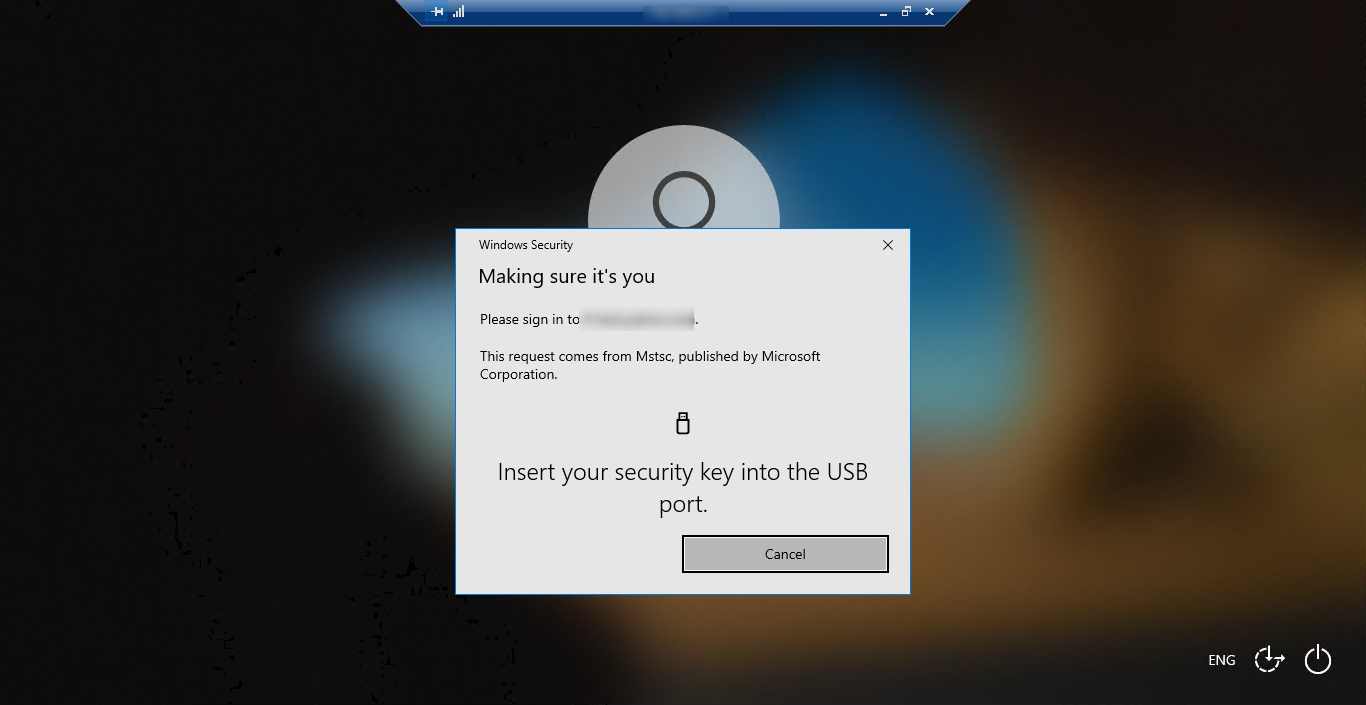
When the source PC is Windows 10
When authenticate on Remote Desktop, use the security functionality that comes standard with Windows to authenticate.
Available authenticators vary depending on the Windows version of the source PC.
As of June 2024, if you wish to use a smartphone as an authenticator, the source OS must be Windows 11.
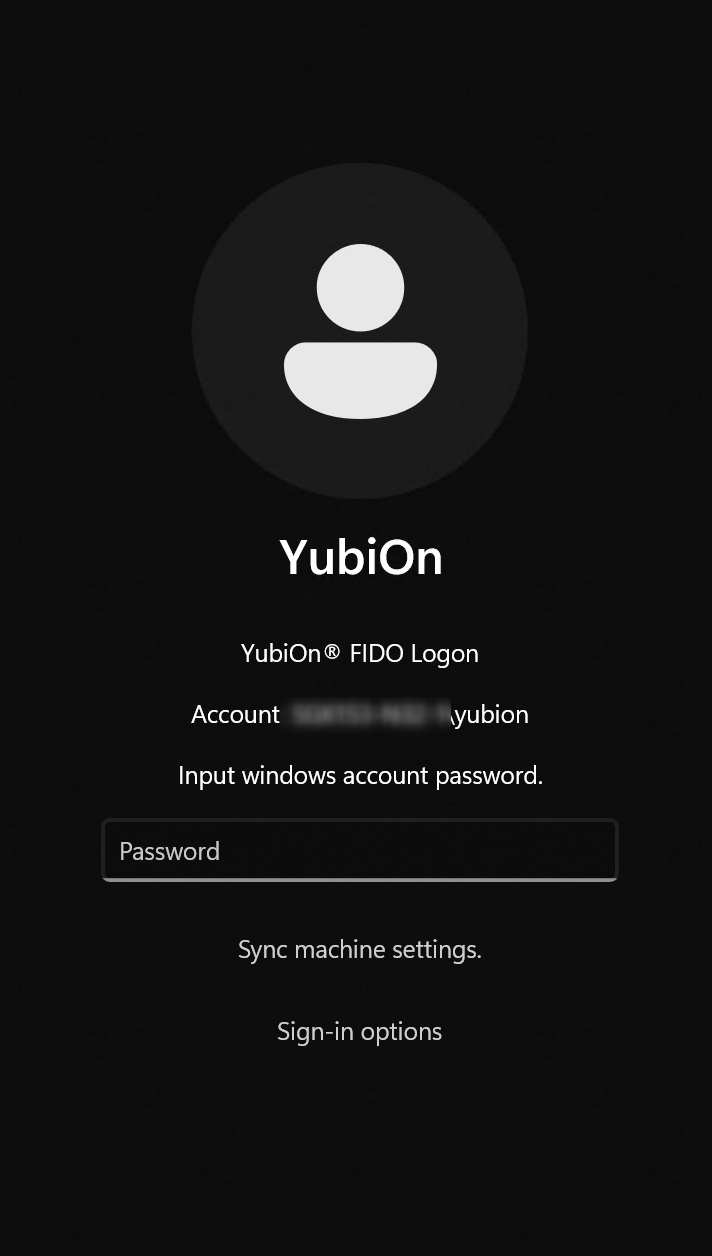
If you are using a FIDO2-compliant security key, such as a PIN or biometric, or a smartphone, the Windows password you enter will be securely stored and will not be required the next time you enter it.
If you change your Windows password, you will need to enter it again.
About Password Cache Regeneration
The password cache is stored using the most appropriate encryption method based on the information obtained during FIDO authentication.
Basically, a password cache is generated and used for each authentication information. However, the password cache may need to be regenerated due to differences or changes in authentication methods, such as the following
- Change of Windows password
- Differences in devices used for smartphone authentication
- Differences in authentication routes (direct logon, remote desktop logon)
- OS and software updates of PCs and smartphones
If you need to regenerate the password cache, you will be asked to enter your Windows password again at the time of logon, so please follow the instructions on the screen to enter the password.
If the Windows logon is successful, the desktop will be displayed.
When logging on via remote desktop, the “Screen lock when authenticator is removed” function is not supported.
Authentication in offline mode
YubiOn FIDO Logon performs online authentication.
However, if the administrator has enabled cache logon (offline logon) in the organization settings, offline logon is possible under the following conditions .
Cache logon must be enabled in the organization settings.
Online authentication must be successfully completed on the PC.
The number of days specified in the organization settings must have elapsed since the online authentication was successful.
About user selection when network level authentication is disabled
If network level authentication is disabled, the user name is basically entered and selected on the logon screen after connecting to Remote Desktop.
However, if network level authentication has been performed at least once, the Windows standard remote desktop application will record the user name, so the user name may be fixed.
The user name information of the remote desktop application is recorded in the following registry key in the source PC.
\HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers\(IP address)\UsernameHint