Log Screen
This screen allows you to view and download the authentication logs of PCs.
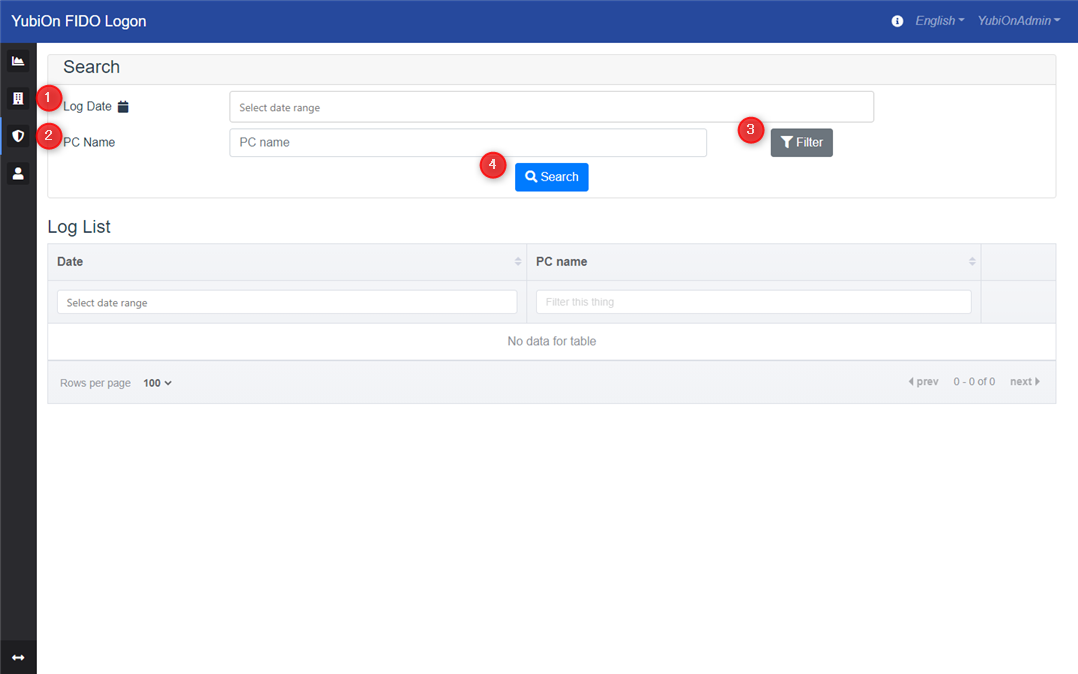
Search
This item is used to search the log.
1. Log Date
This item is used to narrow down the logs to be displayed in the list by date.
2. PC Name
This item is used to narrow down the logs displayed in the list by PC name. The entered string is searched by partial match.
If you select a device with the filter button, the search will be done by exact match.
3. Filter button
This button is used to select a PC name for refinement from the list of registered PCs.
Clicking this button will display a modal for selecting a PC.
4. Search
Displays a list of logs that match the search criteria. If you do not enter any search criteria, all logs will be searched.
PC List
Displayed when the filter button is clicked.
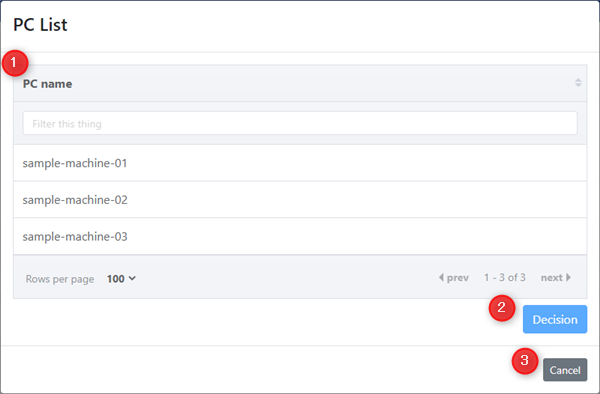
1. PC Name
Displays a list of registered PCs. Select the PC name you want to search.
2. Decision button
This button is used to determine the selected PC.
3. Cancel button
This is the back button without selecting a PC.
Log List
Lists the authentication logs of PCs that match the search criteria.
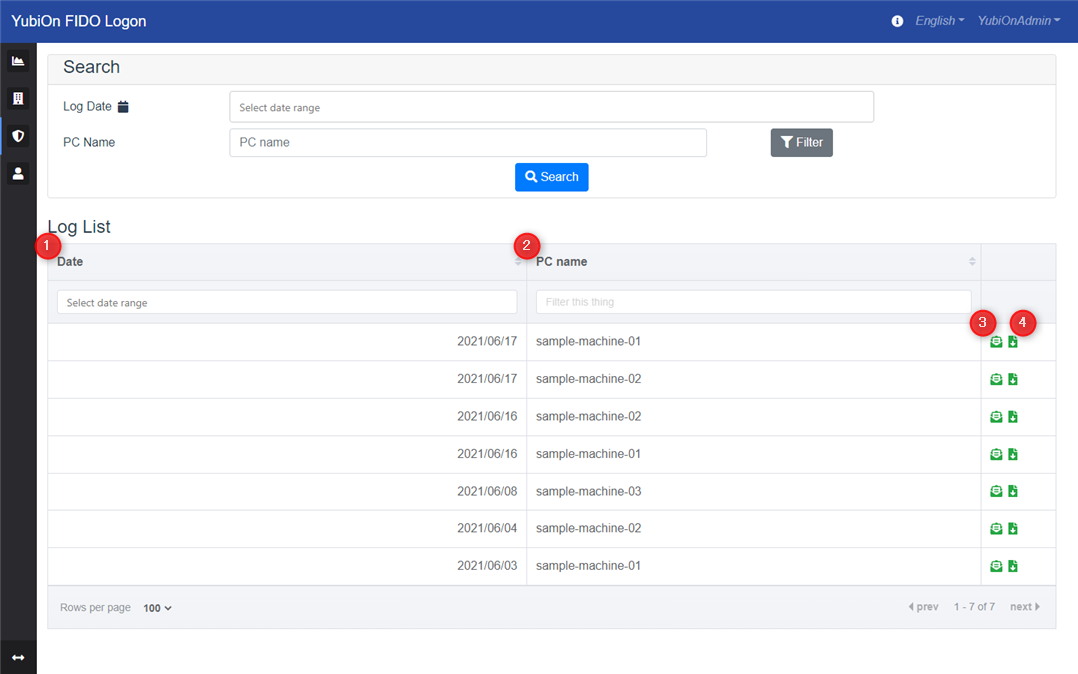
1. Date
Displays the date and time of the log.
2. PC name
Displays the PC name.
3. Detail icon
This icon lists the details of the target authentication log.
4. Download icon
This icon is used to download the details of the target authentication log as a file.
Log Details
Displays detailed information about the selected authentication log.
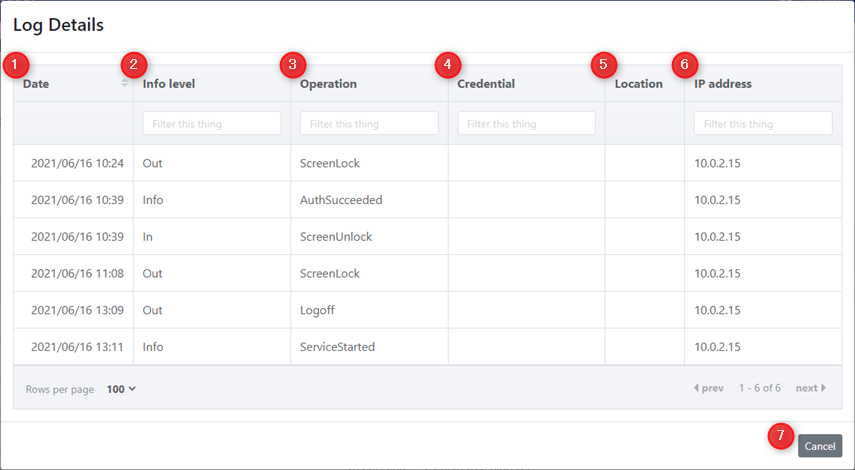
1. Date
Displays the date and time of log writing.
2. Info level
Displays the information type.
3. Operation
Displays the operations that have been performed.
4. Account
Displays the account that performed the operation.
5. Authenticator name
Displays the name of the authenticator used during FIDO authentication. (peration during FIDO authentication only)
For logs prior to October 2024, the authenticator name field is set to the ID of the authentication information (CredentialID).
6. Location information
Displays the Location information obtained. (Only if you were able to obtain one)
7. IP address
IP address will be displayed. (Only if you were able to obtain one)
8. Cancel button
Return to the log list screen.